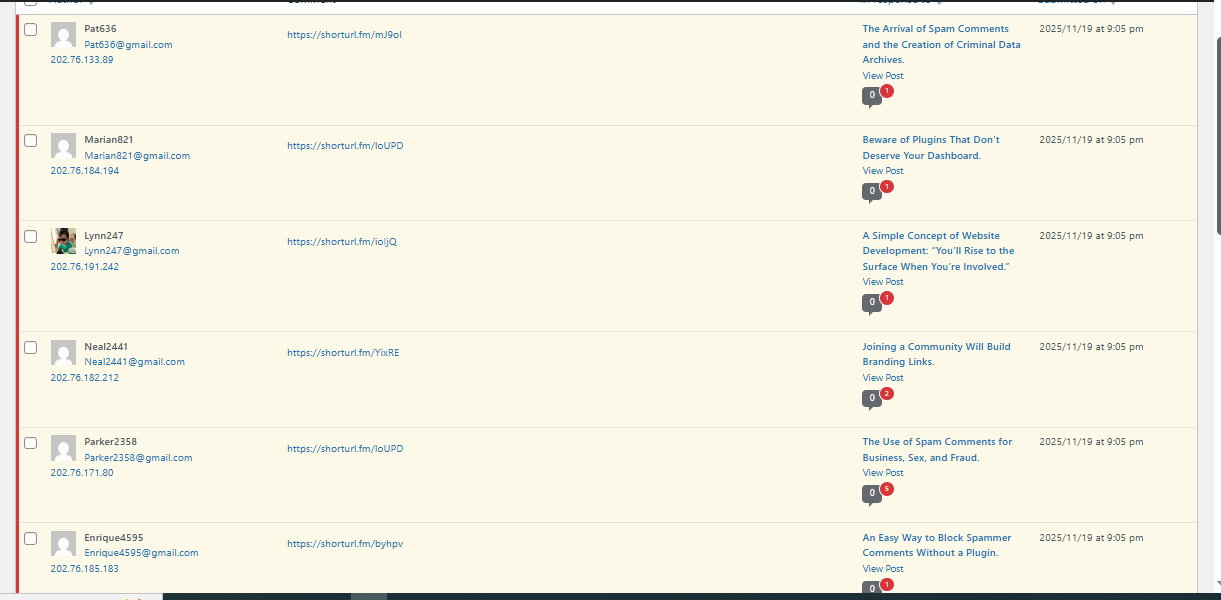
Category: Criminal
-

Spammers’ Lack of Knowledge and Opportunities for Crime.
Spammers have a wide range of opportunities to exploit, particularly by leaving specific comments on various articles and sending emails containing misleading links. All articles published online by authors present opportunities for spammers to exploit by commenting on them, containing malicious information, scams, and hacking information when someone clicks on the link provided by the…
-

Link Mode Exploited by Cybercriminal Gangs – https://shorturl.fm/.
A very popular link used by cybercriminal gangs is https://shorturl.fm/ to carry out their crimes. While not all https://shorturl.fm/ links are spam, they are frequently used by cybercriminals. The https://shorturl.fm/ link is actually a link that functions to shorten an article address or similar content for easier access. However, the https://shorturl.fm/ link has been misused…
-
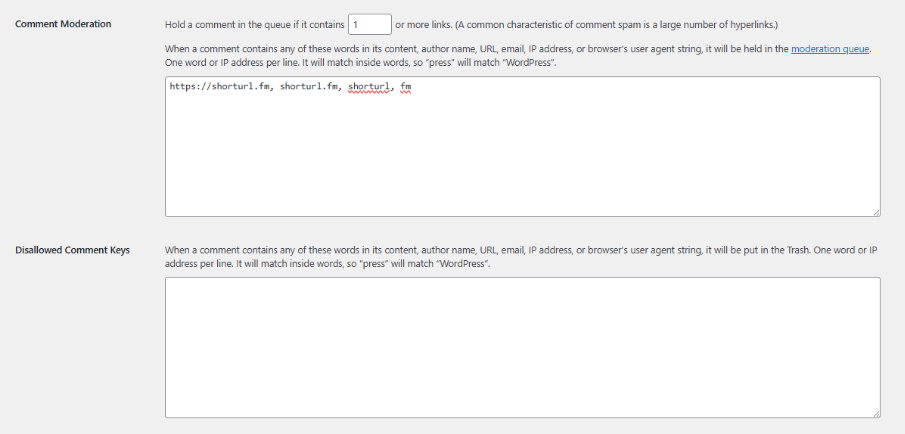
An Easy Way to Block Spammer Comments Without a Plugin.
You can choose whether or not to use a plugin when blocking comments deemed spam on your website. This is a matter of consideration for your interests as a website owner and in managing your website. Several plugins are available on websites, especially WordPress, to anticipate the activities and actions of spammers. All plugins are…
-
Beware of Plugins That Don’t Deserve Your Dashboard.
Plugins are a crucial part of the support system for a website’s development process. They can lead to various improvements in design, website performance, website management, and even task management. A plugin is a system designed to replace coding in website design. Plugins automatically execute various coding tasks depending on the plugin used. With WordPress,…
-

The Arrival of Spam Comments and the Creation of Criminal Data Archives.
Technological freedom has brought a variety of actions that anyone can take as they wish. This time, when receiving spam comments, two comments categorized as spam appeared in an article. The criteria for spam comments can be seen from the comment content, the link shared, the IP address used by the user, and the email…
-

Independent Social Media Projects and a Company’s Business Interests.
Social media users’ ability to understand the various interests of the companies providing social media is crucial for achieving a balance between interests and goals. Social media users must understand the systems implemented by social media companies, as they impact both users and the social media service provider. Generally, social media services have business objectives…
-

WordPress and Bcrypt Make Brute Force Attacks Difficult for Hackers.
Hackers are making various attempts to break into websites. This has further fueled the enthusiasm of program designers to develop stronger and more robust security measures. One remarkable phenomenon is the emergence of Bcrypt in password security. Bcrypt is a hashing algorithm that strengthens password security. Bcrypt is used by various industrial security services, technology…