Every event is a moment that can be used as a topic for discussion in an article. Experience always provides interesting nuances to develop as writing ideas, especially those related to the website development process.
Website owners or managers inevitably encounter various incidents related to website activity, such as the presence of comments that are considered spam or not. This can be analyzed from various comments left by visitors.
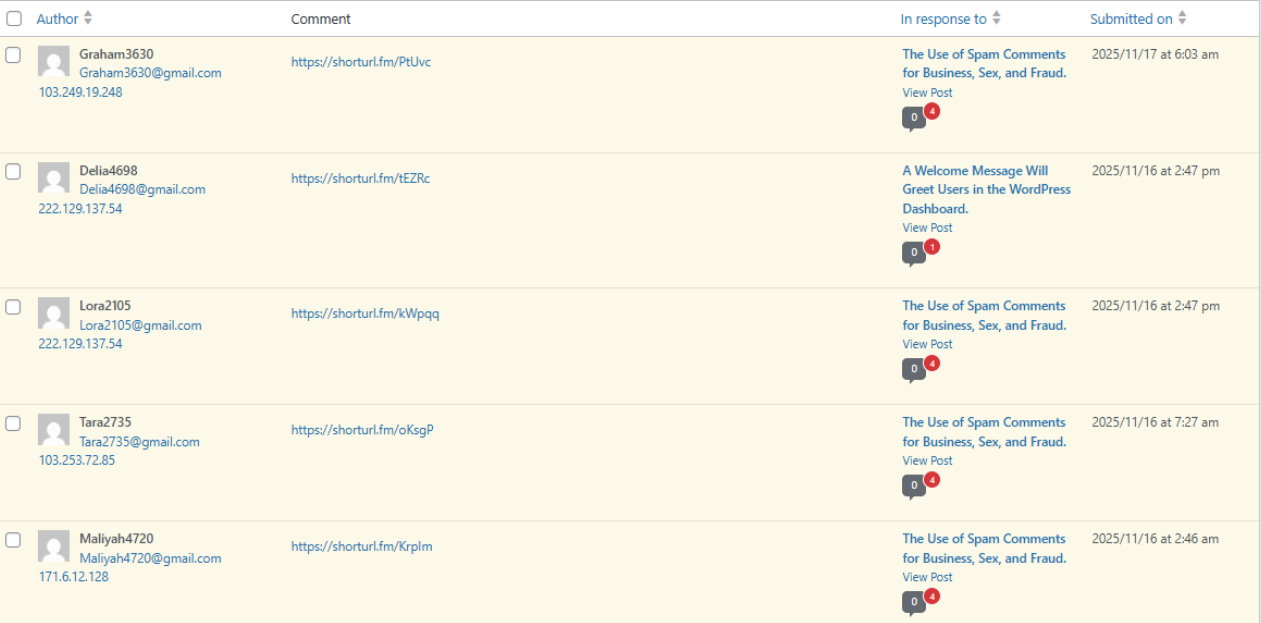
This article contains examples of comments deemed spam, based on an analysis of incidents on the website. Based on several considerations and checks, the comments were determined to be spam.
The image in this article shows an example of a spam comment, illustrating the analysis that the comments were made at approximately the same time. Another factor that can be analyzed is the similarity of the comments made by the spammer and the links shared in the comments.
The IP address used by the spammer is a step that must be investigated, and results show that the spammers use the same location. Although the IP addresses are different, some data is almost identical.
The type of email address used by spammers is an important consideration when determining whether a comment is spam. The similarity of email addresses used by spammers is a factor that can be used as a basis for determining whether a comment is spam.
Other factors used in analyzing and determining whether spam is spam include IP checks and plugins provided for website or WordPress operations.
When spammers leave comments on an article, it becomes clear that illegal activity is easily occurring and proliferating online. This requires understanding from website owners and managers to take action for the development of their website.
There is no wiser approach than taking action to block spam messages. Even IP addresses used by spammers can be reported as misused. Reporting IP addresses as spam is crucial for preventing cybercrime.
When you report an IP address deemed spam, you are taking a beneficial action to protect other users from spammers. This should be an educational approach for all internet users, encouraging them to support each other in eradicating spam and reducing the scope for spammers to operate.
If you allow spammers to roam freely online, you are allowing them the freedom to engage in various activities, thus increasing the potential for criminal activity.
Spammers are typically active online, distributing various links for business purposes, potentially leading to criminal activity. Spammers even group together, distributing the same link to attract visitors and promote something.
Spammers use the same link distribution method to attract visitors to a website. They can even be indicated or suspected of acting as agents paid by a third party to carry out the link distribution activity.
From a business perspective, understanding the suspicion that spammers can use it as a business opportunity or service by distributing various information and links to the public, making it easier to promote something.
This means that spamming can be a business opportunity that offers opportunities to promote a product. Spam can even be used to promote misleading information or malicious links, which can lead to criminal activity.
While some systems automatically consider comments or emails as spam, this is an exception that must be regulated within the system or application.
Websites and email security systems detect potential spam, requiring careful attention and thorough review before marking comments or emails as spam.
Within a system or application, you can designate whether or not something is spam. This can be done through settings that can be changed and adjusted as desired. Make good use of plugins and applications to ensure a comfortable online experience and avoid spam. Be sure to check comments and spam emails when you’re online.
Leave a Reply