Example of a Website Hacking Attack on jybyky.com.
This website will primarily discuss positive aspects of fostering talent and potential through website development. However, several incidents have changed the subject matter, particularly when attacks targeted the website jybyky.com.
In recent weeks, this website has been under attack almost every minute by cybercriminals, prompting changes in the website’s system structure, ultimately leading to a shift in the topic of this article.
Facing repeated attacks from cybercriminals, prudent steps must be taken quickly in designing and managing the website. This is done to enhance security and provide more detailed settings for high-level security.
The attacks on this website have come from various countries around the world, illustrating the vulnerability of cyberspace without multi-layered security.
Despite the minute-by-minute attacks, this website remains safe from criminal activity. This is because several website security standards have been implemented.
To date, this website has attempted to implement multi-layered security by utilizing various potentials without the need for specialized programs, meaning additional security measures are implemented manually and personally.
Returning to the discussion, this website hacking attack is an illegal act. Although this website is simply intended to provide information, share knowledge in a positive way, and help novice writers and website owners who are just starting out in this field.
There is nothing special about this website, but it has become a target for cybercriminals. I am truly disappointed by the incident carried out by cybercriminals in their attempt to hack this website. Although the hacking was successfully resolved, it has caused unrest and concern.
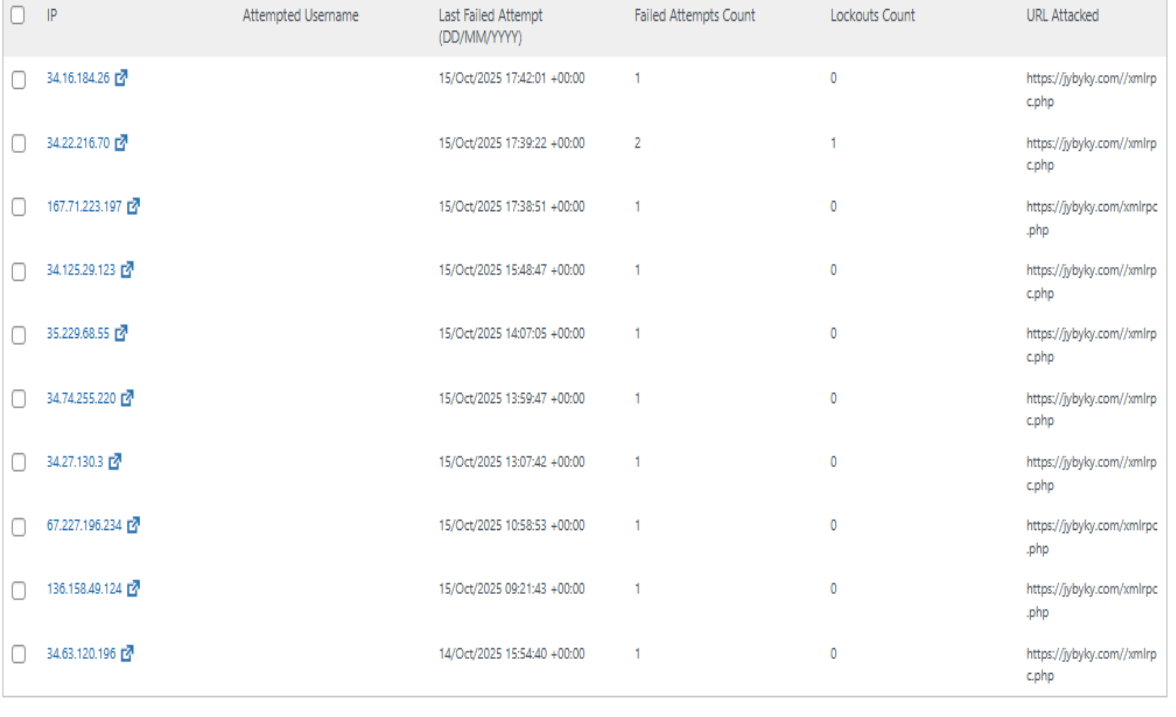
While this article is not specific, it simply provides an overview of examples of hacking that continue to be carried out by irresponsible parties. Several IP addresses have been detected in attacks carried out from various countries.
For information on examples of hacking, please see the images in this article to gain a general understanding of the logic employed by cybercriminals.
Leave a Reply